Mainframe Compliance
DORA
Digital Operational Resilience Act
DORA establishes a comprehensive framework to ensure the operational resilience of financial institutions and their critical service providers. Covering ICT risk management, incident reporting, resilience testing, and third-party oversight, DORA mandates stringent measures to protect against cyber threats and operational disruptions. Compliance requires organizations to proactively monitor their ICT systems, respond swiftly to incidents, and maintain detailed audit trails. MainTegrity CSF supports these efforts by providing continuous integrity monitoring, real-time anomaly detection, and automated compliance reporting, helping organizations align with regulatory expectations and safeguard their mainframe environments. Learn more about DORA compliance for mainframes.
PCI/DSS
Mainframes just don’t comply
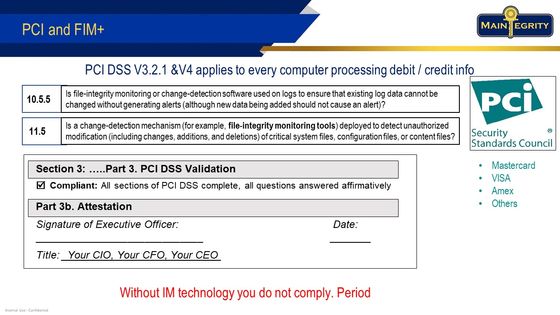
If your mainframe handles credit or debit card information you are subject to the Payment Card Industry’s Data Security Standard (PCI/DSS). Backed by Visa, Mastercard, Amex and most other financial industry, DSS standards have been successful in protecting cardholder data with reasonable checks. Since IBM states that 87% of credit card transactions and 29 Billion ATM transactions are processed very reliably on z/OS every year (as of 2018) PCI DSS will be especially important.
Both DSS V3.2.1, currently in force, and V4 expected by 2024, require File Integrity Monitoring (FIM) to meet sections 10.55 and 11.5. In some cases, “compensating controls” can be substituted for real compliance. These exceptions must always be defended, lower compliance scores and will be scrutinized more carefully under the DSS V4 rules. Further FIM also strengthens many more of the specific controls in DSS. With no generally accepted substitute for FIM processing, if your mainframe is going to comply, you’re going to need FIM+.
FIM+ is also a work saver. It can produce, file, and distribute the required weekly compliance reporting. Since there are no compensating controls to defend, and the needed reports are easily available, FIM+ can shorten PCI audits, reducing the time, cost, and disruption for lengthy audit processes.
Bottom line: MainTegrity is recognized as a thought leader in the PCI DSS space. FIM+ eliminates unnecessary manual effort, improves compliance scores, has better reporting and shortens audits, all while improving your cyber security. This is resulted in many happy customers, but also selection to address the North American PCI conference mainframe ransomware avoidance.
HIPAA
FIM+ helps organizations comply with the Health Insurance Portability and Accountability Act (HIPAA) by continuously monitoring mainframe datasets, providing real-time alerting and an audit trail of all changes. Specifically, FIM+ can help organizations comply with the Security Rule and the Breach Notification Rule of HIPAA. The Security Rule requires organizations to implement appropriate technical and administrative safeguards to protect the confidentiality, integrity, and availability of electronic protected health information (ePHI), including detecting and preventing unauthorized access or changes to ePHI. FIM+ can help organizations meet these requirements by monitoring datasets on z/OS and providing real-time alerting and an audit trail of all changes made to the datasets on a system.
The audit trail provided by FIM+ can demonstrate an organization’s compliance with the Security Rule, helping to avoid penalties for non-compliance.
In case of a breach of ePHI, FIM+ provides the necessary information to comply with the Breach Notification Rule, including the scope and timing of the attack, allowing organizations to quickly notify the appropriate parties and minimize the impact of the breach.
NIST
NIST CSF
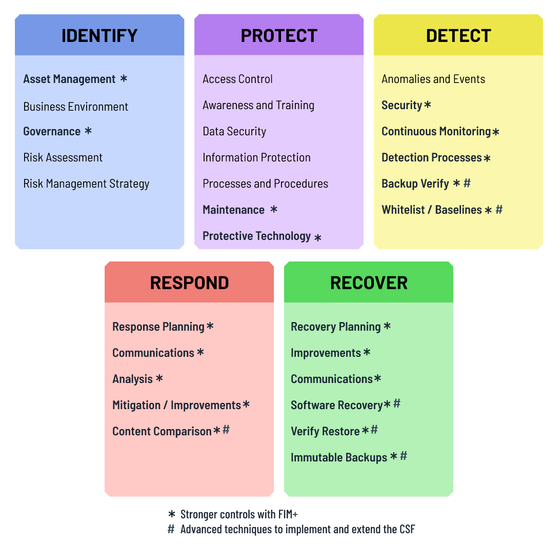
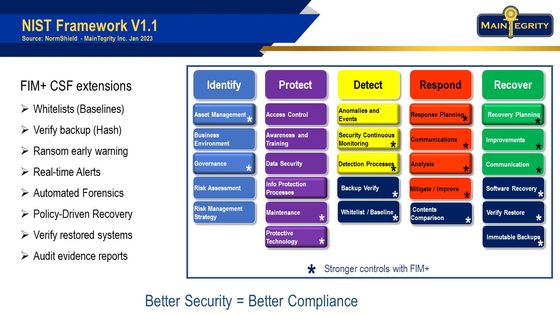
A cornerstone of FIM+ functionality is the NIST Cyber Security Framework, specifically 4 of the pillars Protect, Detect, Respond, Recover. The graphic at left every recommendation that FIM+ implements is shown with a * in the bottom right, nearly all items.
However, FIM+ goes further. The dark blue items are advanced techniques to implement and extend the CSF in meaningful ways. MainTegrity expects to see many of these extensions to become requirements in CSF V2 which is currently in the review process. As such FIM+ provides not only compliance with the current standard but also a degree of future proofing.
An excellent example is creating a mainframe whitelist as suggested by recent bulletins from NIST. This is a foundational function of FIM+. There has never before been a continuously up-to-date whitelist on z/OS which results in an inability to detect compromised components and prevent attacks before they cause damage. The same is true for the FIM+ GUI-based forensics, which result in faster situational analysis and incident response, with greater precision.
MainTegrity has found is that there is a high degree of convergence between the various security standards, many of them with NIST CSF at their heart. Compliance results in better security for your IBM mainframe to protect against increasingly sophisticated attacks, mounted by state sponsored or financially driven motivation. The best response is to prevent, by stepping up your defenses.
FISMA
FISMA (The Federal Information Security Management Act) is a US federal law enacted in 2002 and amended by the 2014, the Federal Information Security Modernization Act. The act affects government agencies and contractors and deals with the protection of information and information systems from threats – unauthorized access, use, modification and destruction. FISMA not only applies to federal agencies, but also to public and private organizations that provide services for government agencies.
To adhere to FISMA compliance, organizations need to implement the controls in the NIST 800-53 publication. Irrespective of whether your organization is subject to FISMA, NIST 800-53 provides valuable insight as to what can be done to protect computer systems. In fact, 800-53 has been adopted and modified by cyber security authorities in many other countries. For instance, you can refer to the links below to find the relevant standards documents; In Canada as istg33, Australia ISM, the UK as cyber essentials, Germany BIS100. Security experts the world over point to 800-53 as an excellent set of controls and along with ISO 27001 should be implemented, on an as needed basis, for all computer systems.
SOX
The Sarbanes-Oxley (SOX) Act was introduced in the USA in 2002 to enhance corporate governance and accountability in financial reporting. SOX compliance involves annual audits of public companies to demonstrate accurate financial reporting and to prevent fraud. Failure to comply with SOX can result in significant fines or even imprisonment.
SOX requires that all financial reports include an Internal Controls Report. This requires meticulous record-keeping and verification of all of a company’s IT assets, including data and computers, with any discrepancies requiring immediate remediation and strict procedures.
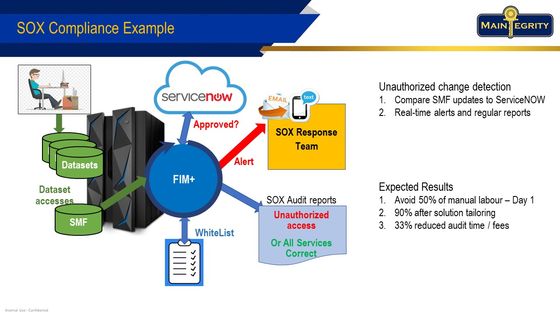
In addition to protecting and detecting internal and external attacks, FIM+ can scan all production files and detect when changes have occurred. Using the ServiceNow gateway, FIM+ can determine if there is a corresponding change request. If a request is found, it is noted and the change passed. When there is no match, FIM+ can send an alert to the SOX team. For them, using the FIM+ forensics browser and recovery assistant can speed resolution. At audit time, FIM+ can automatically produce a complete audit trail, including how the event was resolved, greatly shortening the process.
One organization saw a reduction of up to 90% in staff time and better precision compared to the manual process of reviewing thousands of SMF update records daily and manually checking the change control system for proper approval. With FIM+‘s automated approach, the potential for fines or penalties for non-compliance with SOX can be avoided.
GDPR
GDPR - General Data Protection Regulation
The General Data Protection Regulation (GDPR) mandates that organizations implement appropriate technical and organizational measures to ensure the security of personal data. This includes detecting and preventing unauthorized access or changes, as well as maintaining a comprehensive inventory of all systems and processes that handle personal data.
Under the GDPR framework, compliance is centered around achieving specific outcomes. The Articles 32 and 43 focus on implementing controls that are based on established best practices and standards such as PCI, NIST, and ISO. However, what sets GDPR apart is the level of enforcement it implements through imposing substantial financial penalties. These fines are legally binding and are meant to serve as a deterrent.
Up to 4% of total revenue, some of the more eye-catching fines are: Amazon — €746 million, Facebook — €265 million, WhatsApp — €225 million, Google Ireland — €90 million, British Airways — €22 million. The majority of fines are for willful use of private information for marketing purposes but the BA failure was a more classic breach of private information from cyber attack.
FIM+ can help organizations meet the requirements of GDPR by continuously monitoring systems and detecting any unauthorized changes, providing real-time alerts and an auditable record of all changes. This enables organizations to quickly respond to any potential security issues involving personal data and demonstrate compliance with GDPR requirements. Ignoring GDPR can have severe consequences for an organization.
Cyber Resiliency
Cyber resiliency refers to an organization’s capability to sustain its operations and provide services even in the event of cyber attacks. It involves implementing measures to prevent, detect, and respond to cyber threats, and to recover quickly from any incident that may occur.
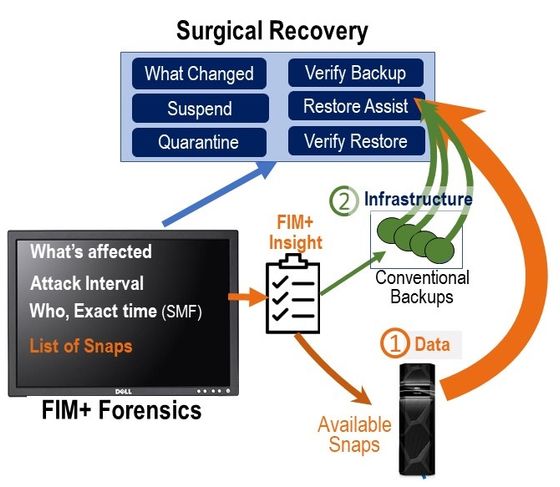
Integrity monitoring raises the bar for resiliency. FIM+ not only prevents and detects malicious attacks but also accelerates recovery. It works with existing security solutions such as RACF, ACF2, TSS, firewalls, SIEMs, and others, on various platforms including z/OS and Cloud, to enhance the overall security of the system.
FIM+ facilitates the recovery process by guiding the response team with a situational analysis and providing information on the latest trusted backups. It can interoperate with various storage solutions and display all accessible backups and snap copies, making data recovery easier. FIM+ can recover only the compromised software and changes, avoiding regression of any undesired changes during the restore process. By doing so, FIM+ not only prevents problems but also helps to reduce the time required for recovery, minimizing the financial, reputational, and operational impact of cyber attacks and ensuring the organization’s operational continuity.