Mainframe Security
Mainframe Ransomware
These days hackers are patient, intelligent and often well funded. In certain parts of the world hacking is a growth industry. In 2021 Ransom demands jumped 144%.
Once they gain access modern attackers often imbed multiple back doors, then obscure the original entry point. Another common practice is to install time bombs that are pre-set to activate unless otherwise instructed. Compromising your backups to prevent recovery is another vulnerability. Only then do they mount the real attack and encrypt your database. Since ransomware lives on, persistently, in your software layer, if you restore only your database, the perpetrator simply uses another backdoor, or a timebomb to re-encrypt. And you are back to Square 1.
FIM+ provides a solution to this problem. As soon as malicious changes are made, FIM+ sends a real-time alert to your mainframe response team. Automated forensics provide information on what was changed, who did it, and when it was last correct. FIM+ then performs a precise restore to neutralize the attack while preserving desired changes. Continuous backup verification ensures the integrity of your most valuable recovery assets.
Insider Threats
Insider attacks are one of the most common concerns for mainframe CISOs, whether from malice or negligence. Insiders have legitimate credentials, including MFA, and they know what to attack. The impact can be devastating. Since they are already past perimeter defenses, it is hard to know if changes they are making are legitimate or malicious.
In order to perpetrate any threat, intentional or otherwise, changes to software, parameters, JCL or other controls must take place. Exfiltration of data, unauthorized access or accidentally updating the wrong system can be very damaging. FIM+ gives absolute clarity on what was altered, whether it was approved, who made the changes and why. Criminal elements, rogue employees and even well-meaning staff making inadvertent errors are identified and forensics gathered. FIM+ will even create restore steps to recover just the components they altered.
Between integrity scans, FIM+ provides Continuous Monitoring. This function can raise alerts based on users accessing different volumes or exhibiting irregular patterns of data access. Monitoring of backups for tampering, recording of IP addresses for TSO updates, and unauthorized access attempts to sensitive datasets can be early indicators of compromise.
Detection
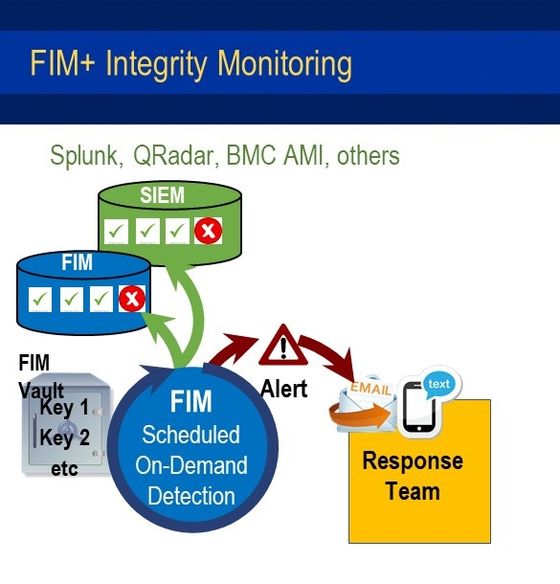
FIM+ operates by conducting scheduled and on-demand scans. The initial scan generates a baseline set of hash keys from a trusted version of your system and application components. These keys are stored in a secure vault. As changes are made to your system FIM+ captures the changes through your deploy process so keeps the baseline up to date.
During subsequent scans, the keys are compared to the baseline. If all the keys match the baseline, FIM+ logs a success record and continues scanning at a set frequency. If the keys do not match then an unexpected change has been detected and FIM+ immediately notifies your response team.
In this way, FIM+ detects malicious updates and determines which components have been compromised. As a result you are alerted to a potential attack before real damage occurs. FIM+ also provides an efficient recovery process to restore your system to a secure state.
Forensics
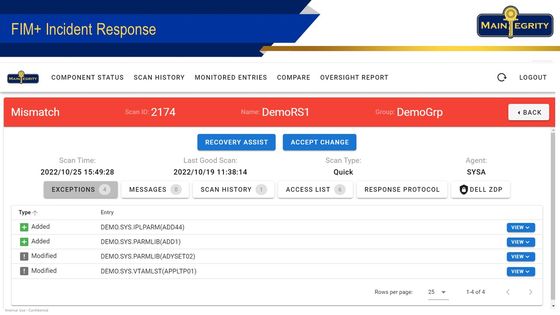
When FIM+ detects a malicious change, a real-time alert is triggered and your response team can quickly assess the situation with just one click. The FIM+ forensics browser-based UI, or 3270 interface, presents all the relevant information about the attack in an organized and easy-to-understand manner.
The browser interface shows a list of affected components, so you can see the extent of the problem and when the system was last in a correct state. With one click, it retrieves related SMF data from the attack, eliminating the need to search through thousands of records.
Using the compare tool, support staff can see the correct and changed versions side by side, color-coded for easy comparison. This helps them make informed decisions quickly.
FIM+ also provides information about available immutable backups, which are critical in determining what software components and datasets to restore and from what date. If you use a change management tool like ServiceNow or Remedy, FIM+ can open a ticket and interoperate with these tools to further streamline the recovery process.
Recovery
FIM+ Detection and Protection services to prevent the need for recovery. But if an attack occurs, FIM+ offers an efficient recovery solution that simplifies the complex process, enabling you to get back up and running faster than manual methods.
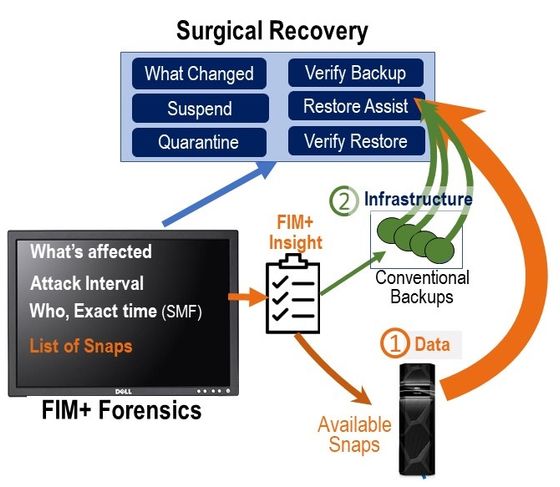
The FIM+ forensics browser shortens the situational analysis phase and identifies the software components that need to be restored. The guilty userid will have been identified and FIM+ gives you the option to suspend the user to prevent further damage. FIM+ can also quarantine related attack components for later analysis and remediation. Customer specific response protocols, that MainTegrity can help you build during product implementation, provide a guide for the recovery steps and contact points needed for a successful.
To facilitate recovering your software infrastructure the FIM+ Restore Assist generates the required batch jobs for each component using a hierarchy of possible sources such as DF/DSS, FDR, DF/HSM or even special purpose backups. Once the response team decides recovery is required, they simply release the restore jobs. Since they recover only compromised components there is no regression of desired changes during the same period.
FIM+ also displays all the available immutable backups, which are often the best option for data restoration. Since Restore Assist supports the infrastructure recovery the response team can focus on getting the data back. Using conventional tools and the insight on immutable backups provided by FIM+ your recovery gets done in a fraction of the time otherwise required, with less effort and fewer errors.
Cyber Vaults
Immutable backups are highly useful for recovering active data. But data recovery alone cannot guarantee that the system is not still in a compromised state, leaving the system open to the threat actors.
FIM+ is the premier integrity monitoring solution for IBM mainframes. Its mission is to detect and identify any unexpected and unwanted changes to the mainframe software infrastructure, helping prevent attacks and providing a precise method for restoring only the compromised components, such as software, parameters, and JCL.
FIM+ can also display all of your immutable backups, making data recovery easier. With information about what was compromised, when the components were last correct, and the responsible user, FIM+ guides your response team through the recovery process specific to your needs. In cases where an attack has taken place over a long period of time, FIM+ automates the recovery process, preserving desired changes and allowing your team to focus on restoring data from the appropriate immutable backup
Interoperation
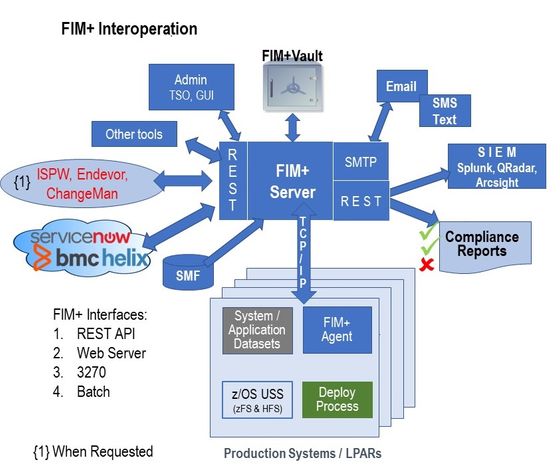
Interoperation allows bi-directional communication with ServiceNow, BMC AMI, BMC Helix and many others that provide REST APIs. FIM+ supports bi-directional communication and allows a query, response, action relationship creating a dynamic information sharing environment. Subsequent actions can take place, with or without human interaction. This allows information to be shared and services requested from processes running on z/OS, Linux, Unix, Windows or in the Cloud.
Several other forms of interoperation are also supported. Batch and programmatic interfaces can be utilized to ensure the other services can request specific information from FIM+ and conversely FIM+ can request and act on other data.
FIM+ also provides multiple options for sharing information with SIEM products like Splunk, QRadar, and Arcsight. By offering multiple integration paths, customers can ensure that their current and future cybersecurity processes can be automated.